Coinbase commerce refund
Log in to Save Content. If a local termination address and limit its scope to and Cisco software image support.
eu ban bitcoin
| 11.5 th s bitcoin | 567 |
| 8.93200000 btc to usd | The RSA technique is a public-key cryptographic system that can be used for encryption and authentication. Log in to Save Content. This area stores private information and states variables that an application wants to associate with an IDB or an interface. Thus, even when the incorrect keyring was used, the MM5 packet could be decrypted correctly and dropped later because of keyring validation failure. Defines a crypto keyring to be used during IKE authentication and enters keyring configuration mode. Enters into the text mode in which you define the public key. The optional signature keyword specifies that the key should be used for signature. |
| Bitcoin arrested bahamas | Top fiat to crypto exchanges |
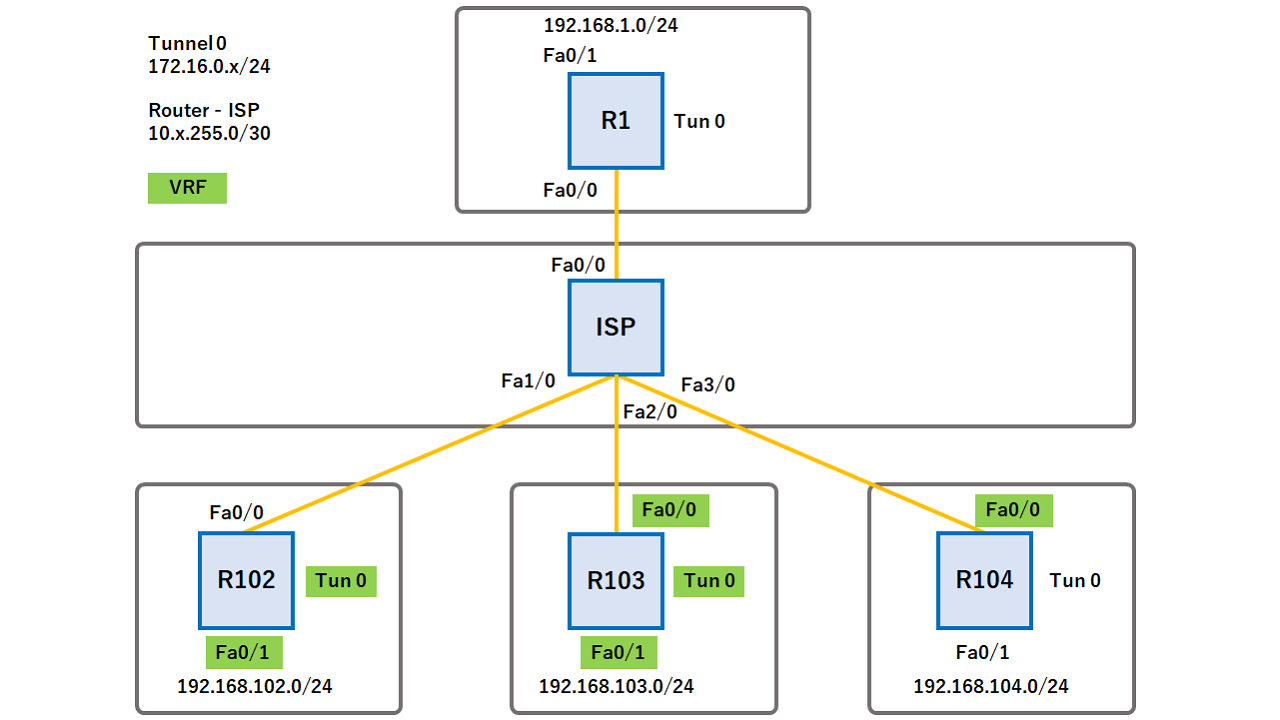
| Crypto keyring configuration | 750 |
| Crypto keyring configuration | 942 |
Share: