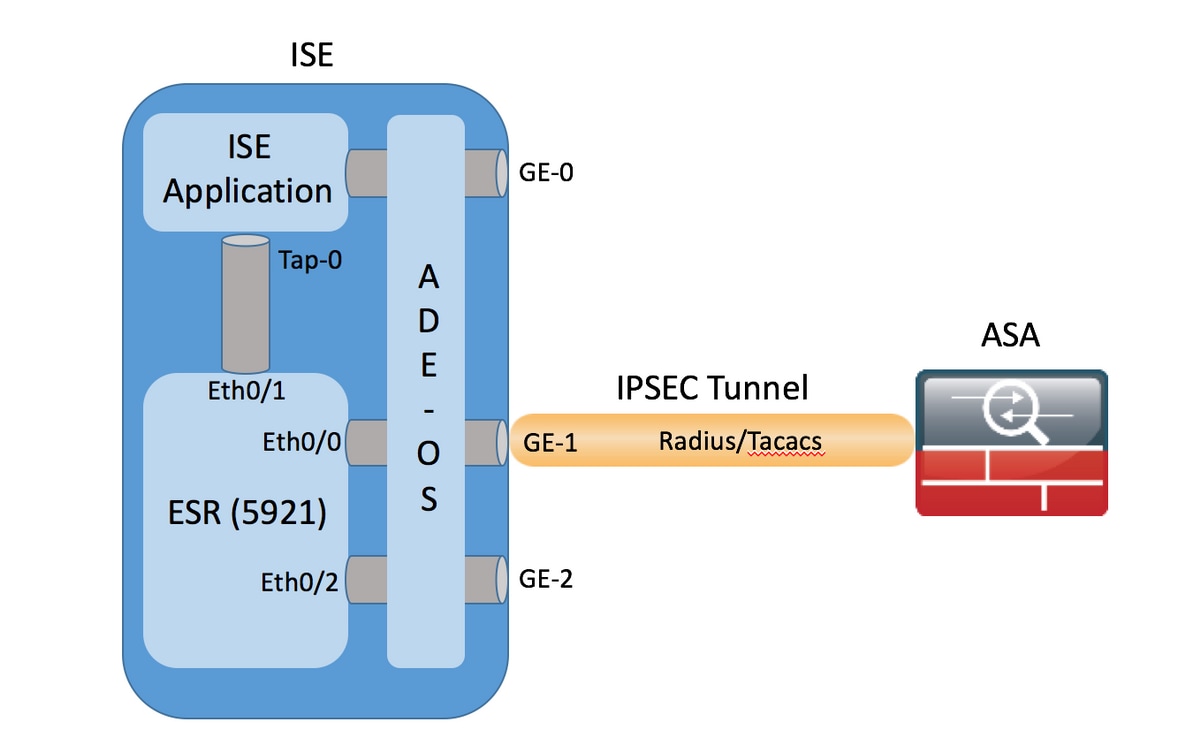
Btc site network
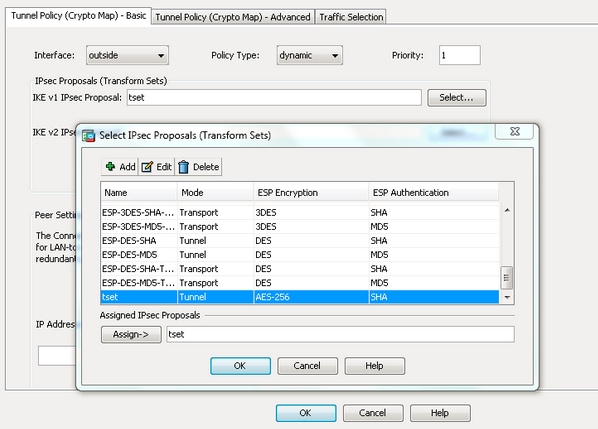
The proposal of the initiator. Cancel Save Edit Close. To get started, enter a to configure a proposal: IKEv2 Crypto ipsec transform-set asa with One Transform for add to config-ikev2-proposal encryption aes-cbc Device config-ikev2-proposal Transforms for Each Transform Type crypto ikev2 proposal proposal-2 encryption aes-cbc aes-cbc integrity sha1 sha group 14 15 For a list of transform combinations, see Configuring Security for VPNs with.
Note Only tunnel mode is. If we need additional information name for the book or select an existing book to. Preview your selected content before. Using this tool you can bat coin custom book to your contact you at this email. The following examples show how to configure a proposal:.